Slovensko:
Ta zaklad je del serije puzzle geo-zakladov:
- Crypto I: Ancient
- Crypto II: Cipher
- Crypto III: Key
Ti trije zakladi vam bodo pokazali svet kodiranja podatkov, ki z informacijsko tehnologijo vedno bolj vdira v vsakodnevno življenje. Ce vas bo tema zanimala bolj lahko vec preberete tukaj. Zakladi somed seboj neodvisni, vendar je priporocljiv gornji vrstni red.
Prvi zaklad te serije je izkoristil trik iz zgodovine. Ta geo-zaklad pa bo ostal v sedanjem casu in vam prikazal osnovno idejo kako kodiramo dandanes, ter zahteval od vas, da nadete pomankljivost, ki vas bo pripeljala do zaklada. Kljub temu, da se dandanes to pocne s pomocjo kompleksnih programov, je uganka zastavljena tako, da jo lahko rešijo vsi. Ni potrebno nikakršnega predznanja s podrocja racunalništva, saj je vse potrebno obrazloženo v naslednjih odstavkih.
Osnovna stvar, ki se je je potrebno zavedati: v racunalniškem svetu vse temlji na številih. Tudi besedilo! To je le zaporedje znakov, in vsak znak je v racunalniku zapisan kot število. Tabelo, ki znakom pripiše ustrezno število imenujemo kodirna tabela. Uporablja se vec takih tabel (ASCII, UTF-8, ...), vendar bo tukaj veljala naslednja tabela z 79 možnimi znaki:
Figure 1
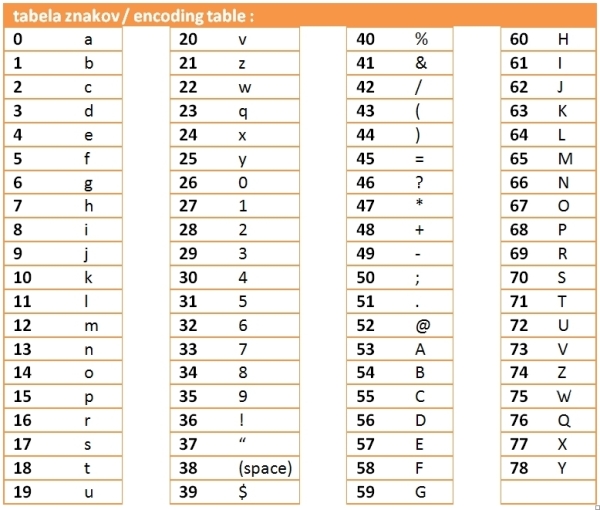 |
Torej, ce v racunalnik vnesemo znak 'A' bo ta zapisan kot število 53, ali ce nam bo racunalnik prikazal število 46, bomo to videli kot '?'.
Oboroženi s to tabelo lahko zakodiramo posamezen znak. Jedro vsakega kodiranja je 'cipher': predpis/algoritem, ki s pomocjo skritega števila (key) pretvori poljubno število x v zakodirano število z. Takšnih algoritmov je ogromno, vendar bo tukaj uporabljen naslednji:
 |
z = ostanek pri deljenu števila (x + key) s številom 79. |
Torej, ce je zacetno število
x=32 in
key=72, potem 32+72=104. Zakodirano število je torej ostanek pri deljenju z 79:
z=25. Z znaki je povsem enako, le da moramo s pomocjo kodirne tabele znak najprej pretvoriti v število, to zakodirati, ter zakodirano število s pomocjo tabele pretvoriti nazaj v znak. Ce ostane
key=72, potem znak 'G' zakodiramo takole:
Figure 2
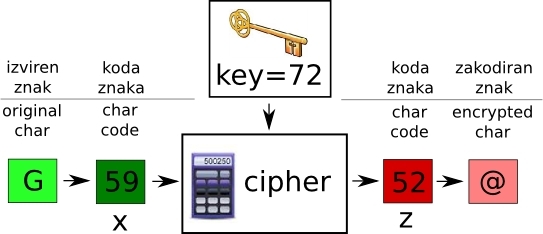 |
'G' je predstavljen s številom
x=59. Cipher torej racuna: 59+72=131. Ostanek pri deljenju z 79:
z=52, kar je število za znak '@'. Torej z
key=72 je znak 'G' zakodiran v znak '@'.
Kar preostane je le, da se zakodira celotno besedilo. Gornji postopek bi lahko ponovili za vsak znak posebaj, vendar se izkaže bolje ce se uporabi naslednja shema:
Figure 3
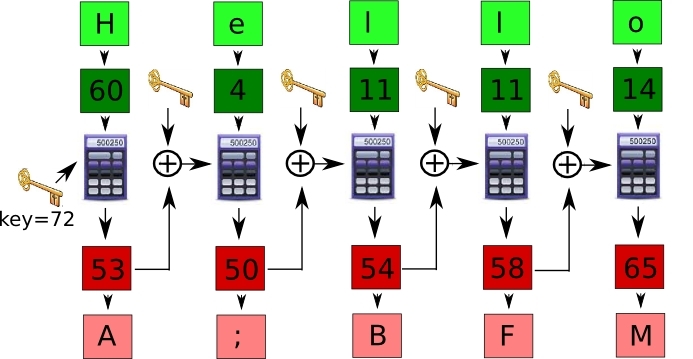 |
Skrivni kodirni kljuc 'key' se uporabi le pri prvem znaku. Pri drugem, namesto njega uporabimo vsoto rezultata z prvega znaka in kljuca 'key', in tako naprej... Na shemi je prikazano kodiranje besede 'Hello', ki se s
key=72 zakodira v 'A;BFM'.
Tako zakodirano sporocilo se lahko prenese do naslovnika, in razumel ga bo le, ce pozna skrivni kodirni kljuc 'key'. Da sporocilo odkodira mora uporabiti nekoliko drugacen cipher:
 |
z = ostanek pri deljenu števila (x + 158 - key) s številom 79. |
ter naslednjo shemo:
Figure 4
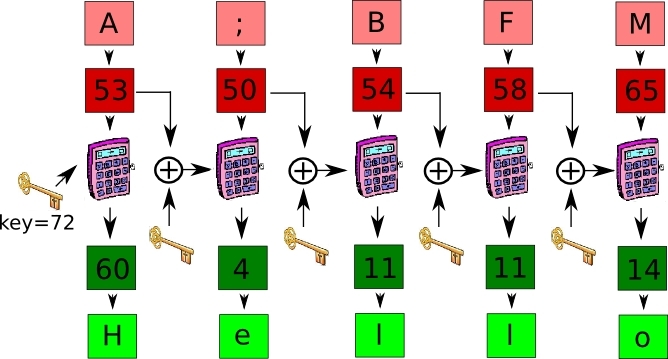 |
Geo-zaklad sem skril nekje v Mariboru. Njegove koordinate N46.????? sem zakodiral v '
-JX6?HRhu' in E15.????? v '
%;Lu8+ENe', vendar se je po nesreci skrivni kodirni kljuc izgubil. Pomagaj mi kljub izgubljenemu kljucu ponovno najti zaklad.
English:
This cache is a part of puzzle geocache series:
- Crypto I: Ancient
- Crypto II: Cipher
- Crypto III: Key
These three caches will lead you into the world of cryptography that more and more becomes a part of everyday life. If you want to know more about the topic you can read here. The caches are independent, however the above order is recommended.
First cache of this series used a trick from history. This cache will stay in present times and it will show you the basic ideas of modern cryptography. Finding out its weakness will lead you to cache coordinates. Even though this things are done using more complex algorithms, this puzzle is set up in a way that anyone can solve it. No previous knowledge on the subject is needed since everything is simply described in the next paragraphs.
Important thing to understand: in computer world everything is based on numbers. Even text! Text is nothing but series of characters, and each character (char) is in computer written as a number. The table that links the characters to their respective numbers is called encoding table. There are more such tables used (ASCII, UTF-8, …), but here the table in figure 1 will be used.
So if we input char 'A' into the computer, it will be stored as number 53, or if 46 will be returned to us we will see it as '?'.
Armed with this table we can encode single char. The core to every encoding is the 'cipher': algorithm that with the use of the secret number (key) transforms given number x into the encrypted number z. There are many different ciphers, but the following will be used here:
 |
z = leftover when dividing (x + key) with 79. |
So, if the number
x=32 and
key=72, then 32+72=104. The encoded number is therefore the leftover when dividing with 79:
z=25. It is identical with chars, one only has to convert a char into the number with the encoding table, than encode the number, and finally use the encoding table to convert it back to char. If we leave
key=72, than the char 'G' encodes like shone on figure 2. 'G' is represented with the number
x=59. Cipher calculates:
59-72=131. The division leftover is:
z=52, which is the number for the char '@'. In short, with the
key=72, the char 'G' gets encoded in char '@'.
What is left is to encode the entire text. The above procedure could be repeated in exactly same way for each char in the text, however it turns out better if a scheme shown in figure 3 is used.
The secret encoding key 'key' is used only with the first char. When encoding the second char a sum of 'key' and z value of the previous char is used as a key, and so forth … Figure 3 shows the encoding of word 'Hello', that, whit the key=72, encodes into 'A;BFM'.
Such encoded message can be delivered to the recipient, and he will understand it only if he knows the secret 'key'. To decode the message a bit different cipher must be used:
 |
z = leftover when dividing (x + 158 - key) with 79. |
along with the scheme in figure 4.
I hid the geocache somewhere in Maribor. I encoded its coordinates N46.????? into '
-JX6?HRhu' and E15.????? into '
%;Lu8+ENe'. The encoding key 'key' got lost. Can you help me find the cache?