Security by Obscurity
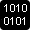





In cryptography proper, the argument against security by obscurity dates back to at least Kerckhoffs' principle, put forth in 1883 by Auguste Kerckhoffs. The principle holds that design of a cryptographic system should not require secrecy and should not cause "inconvenience" if it falls into the hands of the enemy. This principle has been paraphrased in several ways:
- system designers should assume that the entire design of a security system is known to all attackers, with the exception of the cryptographic key.
- the security of a cryptographic system resides entirely in the cryptographic key.
- in the 1940s, Claude Shannon put it bluntly; "the enemy knows the system".
The greater the number of points of compromise in a system, the greater the chance that an attack on one of those points of compromise exists, or will be developed. Systems which include secrets of design or operation which are also points of compromise are less secure than equivalent systems without these points of compromise if the effort required to obtain the vulnerability caused by the secret design or method of operation, and the effort to exploit this vulnerability is less than the effort required to obtain the secret key. The security level of the system is then reduced to the effort required to exploit the vulnerability.
For example, if somebody stores a spare key under the doormat, in case they are locked out of the house, then they are relying on security through obscurity. The theoretical security vulnerability is that anybody could break into the house by unlocking the door using that spare key. Furthermore, since burglars often know likely hiding places, the house owner will experience greater risk of a burglary by hiding the key in this way, since the effort of finding the key is likely to be less effort to the burglar than breaking in by another means. The owner has in effect added a vulnerability—the fact that the entry key is stored under the doormat—to the system, and one which is very easy to guess and exploit.
[Wikipedia]
Cache contains 8GB FTF-prize and some other technical items with the logbook.