This is the 6th cache in my Spycraft series. This geocache is a bit of a departure from others in the series. Rather than telling a specific story, this geocache focuses on the general topic of Tradecraft (a general term that is given to techniques used by spies for field operations). Although this puzzle is harder than most of the Spycraft series, I have endeavored to make it accessible to anyone who has interest, and as always I will answer any questions you have. Once you solve the puzzle and get to the field, you will be able to practice your own tradecraft a bit.
I was listening to my shortwave radio the other night, and heard a very strange broadcast. I have no idea what the source of the broadcast was since shortwave frequencies tend to bounce off the atmosphere and can travel for a distance, but the station appeared to be broadcasting at very high power so it could have been located anywhere in the world. For lack of a better name I'll call it "Yankee Doodle" Station since the broadcast consisted only of the song Yankee Doodle and a female voice reading lists of numbers. Fortunately I was able to switch on my recorder quickly and capture most of it:
"Yankee Doodle" Station on Google Drive
Curious about what this might be, I did some research and discovered that these stations appeared on the airwaves after World War II. They are called OWVL (One Way Voice Link) stations or Numbers Stations and are believed to be a way to communicate instructions to spies working in the field. According to Wikipedia, "Although no government has acknowledged operating one of these stations, a 1998 article in The Daily Telegraph quoted a spokesperson for the Department of Trade and Industry (the government department that, at that time, regulated radio broadcasting in the United Kingdom) as saying, 'These [numbers stations] are what you suppose they are. People shouldn't be mystified by them. They are not for, shall we say, public consumption.'"
Anyone with a shortwave radio can intercept these broadcasts, so they must be encrypted in some way. According to Robert Wallace and H. Keith Melton's book Spycraft, "The only item [KGB double agent] Oleg Penkovsky used that could properly be called advanced tradecraft was his 'agent-receive' communications through a one-way voice-link. These encoded messages, known as OWVL, were broadcast over shortwave frequencies at predetermined times from a CIA-operated transmitter in Western Europe. Penkovsky listened to these messages on a Panasonic radio—strings of numbers read in a dispassionate voice—and then decoded them using a one-time pad". My research turned up a couple examples of One Time Pads that were found in the personal effects of captured enemy agents:

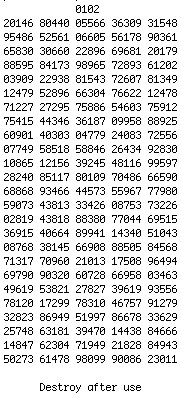
The techniques for encrypting (by subtracting each digit of the pad from the corresponding digit of the message, left to right, without borrowing) and decrypting (by adding each digit of the pad to the corresponding digit of the message, left to right, without carrying - also called Mod 10 addition) using a one time pad are straightforward and fairly well known, but most transmissions will probably involve text, not numbers. A method is needed to convert the information to numbers that can be transmitted. My research turned up a technique used by KGB agents during the Cold War called the straddling checkerboard such as this example.
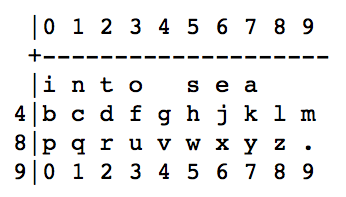
The first row of the checkerboard is usually an easy to remember anagram of the most common letters in the spy's language (ETAOINS in English). Placing these letters on the top row allows each to be transmitted by a single digit (e.g. E=6). Less often used letters require two digits (e.g. J=46 in this example). Using the checkerboard above, "GEOCACHE" would become "44 6 3 41 7 41 45 6". Obviously this is not a very secure encryption as it is a simple substitution cipher and if the encrypted message were long enough it could be broken using pattern and frequency analysis. Combined with the One Time Pad, however, the encryption is completely secure.
With this information, I felt I had a complete picture of how the numbers messages are created and what they might be used for. To transmit a message, it might first be converted to numerical form by using a straddling checkerboard. The results would then be further encrypted by using a one time pad, and then transmitted by the numbers station.
When the field agent intercepts the transmission, she must be careful to use the correct pad sheet and straddling checkerboard. To decrypt the message, each digit is added to the corresponding digit of the pad, left to right, mod 10 (without carry.) The straddling checkerboard is then used to convert the result back to plain text.
This method of deciphering messages is relatively fast and easy for a field agent, requiring only pencil and paper, and is a form of 2-Factor Authentication. In order to decrypt the message, one would need both the keyphrase for the straddling checkerboard (something he knows) and the correct sheet of the one time pad (something he has).
Since the Numbers Stations broadcasts are one-way, how would a field agent get information back to the agent's handler? Again, according to Spycraft, the most common techniques are brush passes (transferring information to another perhaps by slipping a USB drive into a pocket or by concealing a document in a newspaper) and dead drops. Dead drops are used to pass items between two individuals using a secret location and thus does not require them to meet directly. Dead drops may be hollow spikes inserted in a crack in a wall, hidden in a log or under a rock, or in another location that is easily accessible but unnoticeable to an ordinary person.
Disclaimer: this geocache description contains links to files containing details needed to find this geocache. As the cache owner, I represent that these files are safe to download although they have not been checked by Groundspeak or by the reviewer for possible malicious content. Download these files at your own risk. Exact behavior will depend on your specific computer and its settings, and if you have any difficulty please let me know.

You can validate your puzzle solution with certitude.
